Investigations of cyberattacks and data breaches often reveal the initial access vector to be a phishing email. Phishing provides threat actors with a foothold from where they can achieve an organziation-wide compromise, so teaching employees how to identify phishing emails is one of the most important steps to take to improve your organization’s security posture. Businesses that train employees how to identify phishing emails and regularly reinforce the training can greatly reduce susceptibility to phishing and achieve a significant return on their investment in training.
What is Phishing?
In order to reliably identify phishing emails, it is important to understand what phishing is and why phishing attacks are conducted. Phishing is a form of social engineering, which is the manipulation of individuals into taking actions that they would not normally take. Most commonly, phishing involves sending emails that trick the recipient into disclosing sensitive information such as login credentials.
If a person walks up to you in the street and asks for your email address and password, you naturally would not tell them, but that is exactly what cybercriminals do with phishing. The difference with phishing is cybercriminals provide a credible reason for disclosing the information, the attacker often impersonates a legitimate company, trusted individual, or other reputable source, there is usually a sense of urgency, and a threat of negative consequences if no action is taken.
The aim of phishing is to get a malicious message in front of a person and trick them into disclosing sensitive information or giving a threat actor access to the user’s device or network. It is far easier and requires less skill to conduct a phishing attack than it is to exploit vulnerabilities in software, and much quicker than conducting a brute force attack to guess a user’s password.
Phishing campaigns often involve huge numbers of emails sent to random recipients in the hope that some of those individuals will respond. These campaigns require little skill, and are automated so they require little effort, and enough people will respond to make the campaign worthwhile. Phishing campaigns may be much more targeted and can be conducted on groups of individuals using lures that have been carefully crafted to maximize the probability of a response, such as targeting the employees of a specific company. The most sophisticated campaigns are laser-focused and target only a few individuals, sometimes a specific individual. These phishing attacks are often referred to as spear phishing, and this approach makes it much harder to identify phishing emails, and these attacks are highly effective.
The Different Types of Phishing
The most common type of phishing involves messages sent via email, but phishing can take place using any method of communication. The popularity of mobile phones, social media platforms, instant messaging services, and the widespread use of QR codes have given cybercriminals a variety of ways to steal information. The majority of phishing attempts occur via email, but it is important to be aware of these other forms of phishing.
- Smishing (SMS) – The use of SMS messages to direct users to a malicious website, often masquerading as security alerts.
- Vishing (Telephone) – A phishing attempt over the telephone, often used in tech support scams.
- Quishing (QR Codes) – The use of QR codes that direct users to a malicious website that spoofs a trusted brand.
- IM Phishing (Instant Messaging) – A phishing attempt via instant messaging services such as WhatsApp, Messenger, or Discord. Often conducted to trick the user into installing malware or visiting a malicious website.
- IVR Phishing (Telephone) – IVR phishing, or Interactive Voice Response Phishing, uses automated calls with pre-recorded messages, often impersonating a bank, where the user is tricked into disclosing sensitive information to confirm their identity or financial information.
- Callback Phishing (Email, SMS, IM, and telephone) – Callback phishing involves establishing contact via email, SMS, social media, or instant messaging platforms and convincing the user to call a number, with the phishing taking place over the phone. The initial message often warns of an upcoming charge to an account.
Phishing Emails: Statistics you need to know
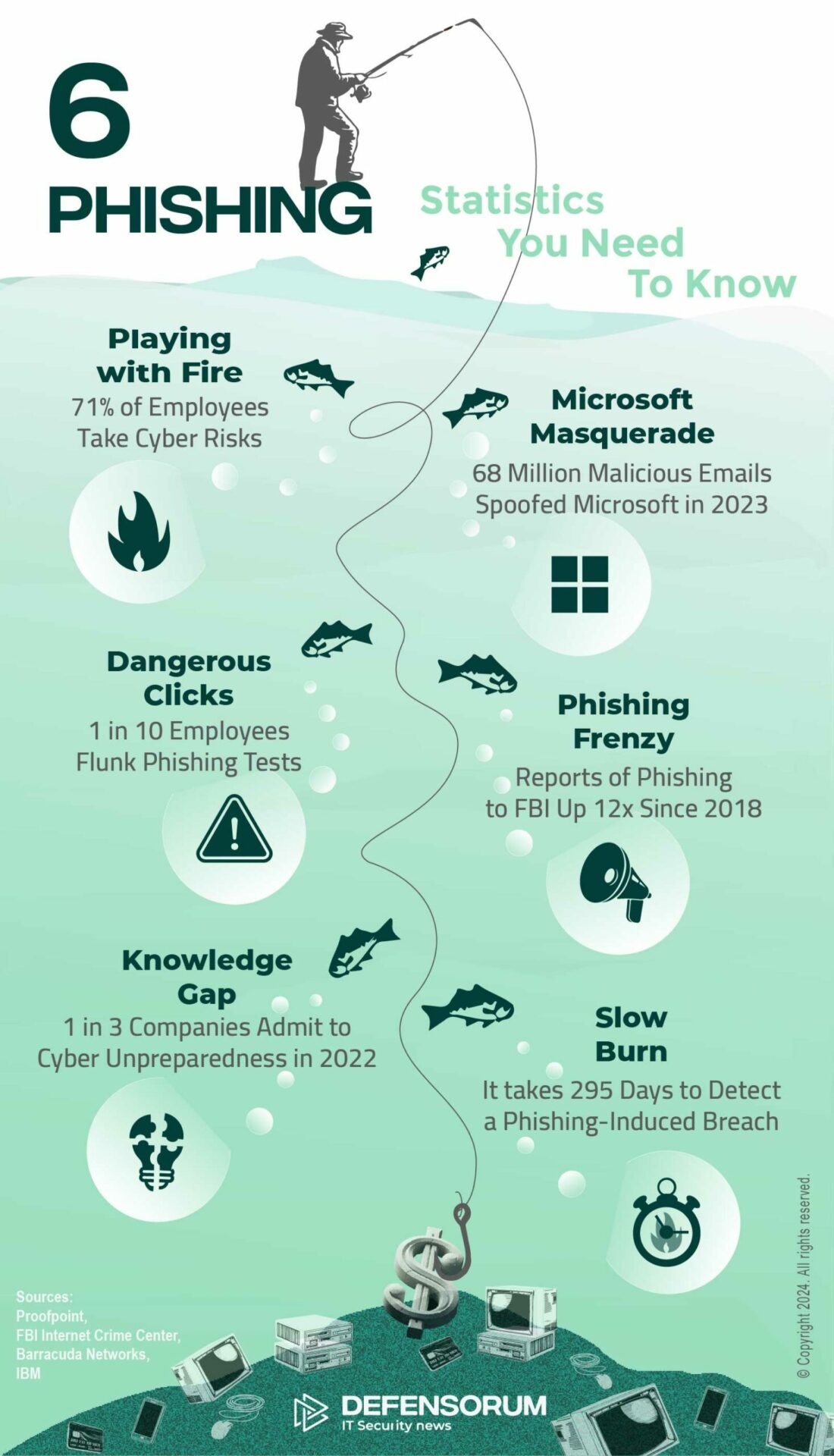
How to Identify Phishing Emails and Other Phishing Scams
Everyone should be aware of how to identify phishing emails but businesses should ensure that they provide security awareness training to the workforce and teach employees how to identify phishing emails. Public awareness of phishing has improved greatly over the past few years, but cybercriminals are conducting sophisticated attacks.
Around a decade ago, phishing emails were relatively easy to identify due to grammatical errors, spelling mistakes, and implausible lures such as Nigerian princes offering large cash payments. Phishing emails today often bypass email security solutions and it can be very difficult to identify phishing emails. Scammers are now using artificial intelligence technology, not just to craft grammatically perfect emails but also to develop new and convincing lures and personalized campaigns.
The key to identifying phishing emails is awareness and preparedness. The risks of phishing need to be explained to employees and they should be trained to be constantly on the lookout for phishing emails and other scams as a phishing email can land in an inbox at any time. Employees should be made aware that they are likely to be targeted and that email security defenses can be easily circumvented. Employees also need to be trained on how to identify phishing emails and be given practice at identifying phishing emails through simulated phishing campaigns.
Training Employees How to Identify Phishing Emails
The key to effective phishing training is to provide it regularly throughout the year. Regular training makes it clear to employees that phishing is a real and pertinent threat and something to be taken seriously. The aim is to develop a security culture where every employee is constantly on their guard, suspicious of any email they receive, and conditioned to stop and think about any action requested in an email, SMS, instant message, or telephone call and never to blindly trust a request because it appears to have been sent by a trusted person.
Employees should be told to be suspicious of any message that requires them to click a link or open an attachment. They should check the true definition of any hyperlink by hovering their mouse arrow over the link and comparing the link to the email address/domain of the sender. If the email has been sent internally and is unusual, they should make a quick call to the sender to verify the legitimacy of the message. Perhaps the most important element of phishing defense is to educate employees never to disclose any credentials, financial information, or other sensitive information via email, SMS, or instant messaging service, and if they are directed to a website and are asked to log in, to check the full URL and ensure that it is legitimate.
Training content should be regularly updated with real-world examples of the latest tactics and techniques used by phishers since phishing tactics are constantly changing.
The Common Indicators of a Phishing Attempt
The common indicators of a phishing attempt all employees should be trained to recognize and report if encountered. Over time, looking for these red flags will become second nature.
- Unsolicited message
- Unknown contact
- Inconsistencies in email address, domain name, and message content
- Unfamiliar tone or greeting
- Unusual file attachment
- File attached when the information could easily have been included in the message body
- Unusual request
- Grammatical errors and spelling mistakes
- Urgency
- The threat of negative consequences
If something doesn’t seem right, employees should be instructed to report it to the IT security team and let them investigate.
Reinforce Training with Phishing Simulations
Security awareness training should teach employees how to identify phishing emails and other scams, but they should also be given practice at identifying phishing. Phishing simulations allow businesses to assess employees and determine if the training has been understood, and if it is being applied. Phishing simulations are not about catching employees out, they are an important element of training. If an employee fails a phishing simulation, they can be provided with further training to increase the chances of them identifying phishing attempts in the future. Phishing simulations also give businesses data that allows them to measure the return on their investment in training and how susceptibility to phishing is being reduced.







